Permutations
An important object in discrete mathematics is called permutation - a bijective mapping between set and itself. From Theorem 241, there are a total of permutations on a set of size . For instance, when , a bijective mapping can be defined as , , and .
We can write in a two-row representation:
The first row lists all elements of and, under each element , we list right under it. In fact, we only need one line to represent such a permutation: Just take the second line , which means that , and . Note that such a representation suffices since we know that the permuted items are listed under a fixed total order of (in this case the natural increasing order ).
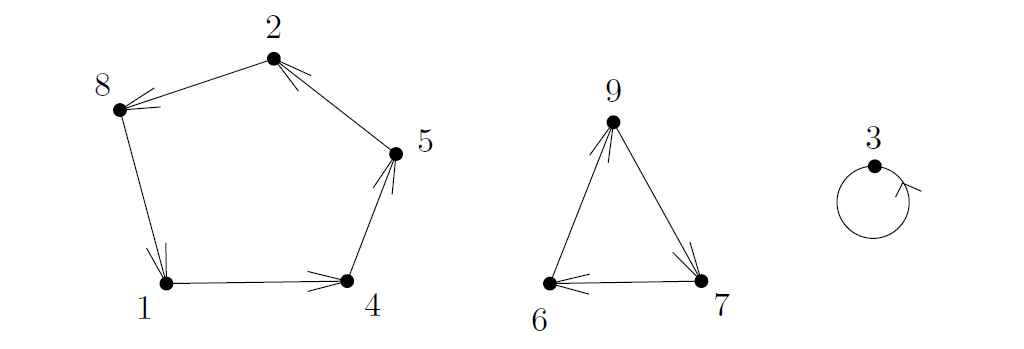
Figure 11 shows a graphic representation of permutations where an arrow from to represents . It is easy to see (by picture) that each permutation has a representation that is a union of disjoint cycles. Again, no matter how you try to draw a permutation, you will see this fact. So it is obvious in drawing, but how do we really define these cycles formally?
Let and be two permutations on . Define as . Notice that is also a permutation on .
We need to argue one-to-one and onto properties. For the one-to-one, assume that ; so . Since is one-to-one, we have ; since is one-to-one, we have . To show the onto property, consider . Since is onto, we have that there exists for which ; since is onto, there exists for which ; therefore, .
For any permutation , we define as the permutation that is a -fold composition of with itself, i.e., and . Define the relation on the set where if and only if there exists such that .
Prove that is an equivalence relation and that its equivalence classes are the cycles of .
Define the identity permutation on as for all .
Let be a permutation. Prove that there exists integer for which . As a bonus, describe an algorithm that, given a permutation , computes the minimum value of satisfying the former property.
Derangements
Now we will consider an interesting example of counting that requires non-trivial, creative thinking. Suppose there are students in class, and we (teachers) already graded the student's homework. If we shuffle the graded homework at random before returning them to students, how many students should we expect to receive their own homework? This is a non-trivial question, and we will see several ways to answer this question.
We say that a permutation on 2 is a derangement if for all . In other words, does not have a fixed point.
The question here is, out of the permutations, how many of them are derangements?
Let be the set of derangements on and be the number of such derangements. We will prove the following recurrence:
We want to count the number of derangements on . First, notice that can map to possibilities (anything but ). We partition the derangements in into sets based on this value, i.e., , so we have that . By a bijection argument, it is easy to see that the sets are of equal size, so we have that .
For simplicity, denote by . We further partition into and based on the value of :
The key observations are that: (i) there is a bijection between and (this is very easy to see) and (ii) a bijection between and . In the exercises, you will formally prove these.
Formally complete the proof of the above theorem. In particular,
- describe a bijection between and for all ,
- describe a bijection between and , and
- describe a bijection between and .
We want to remark that the above theorem immediately implies a computational solution for the number of derangements. With the recurrence relation, it is relatively straightforward to code a dynamic programming (DP).
Derive the following explicit formula for :
Hint: Define . Write the recurrence for and solve it.
Mathematical theory of sorting
In computer science, we encounter permutations very often, most notably in the context of sorting. In this section, we will treat sorting as a purely mathematical topic. A sorting algorithm can be seen as a mapping that takes a permutation as input and performs a sequence of exchange operations until becomes an identity permutation . A good sorting algorithm is one that uses as small number of exchange operations as possible.
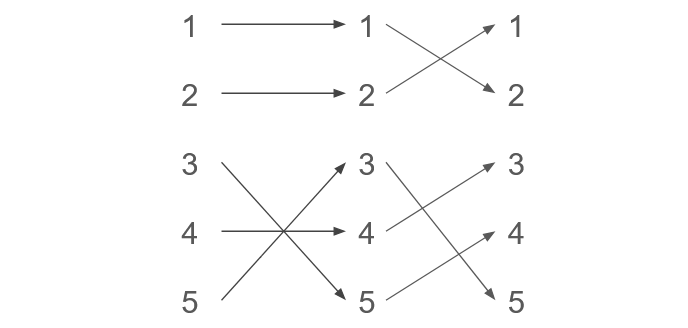
An exchange operation can be seen as composing the input permutation (the unsorted elements) with a swap permutation: , and for . Intuitively, if we represent a permutation in a one-line notation, applying the composition would exchange the numbers in the -th and -th position of the permutation. See Figure 12 for illustration. The following claim makes this discussion formal.
If and , then
Therefore, a sorting algorithm can be seen as, on input permutation , output a collection of so that . For instance, to sort a permutation , we can compose with , and gives us an identity permutation.
Let be a permutation. We say that is an inversion of if and . Denote by the set of all inversions of . This notion of inversion captures exactly the locations of that are currently in an "swapped" relative order and need to be "inverted" somehow. Notice that the identity has , and the reverse permutation has inversions. In this way, measures how far is from an identity permutation.
Prove that is transitive (i.e., prove that if and are inversions, then so is )
The concept of inversion can be used to analyze the performance of some natural sorting algorithms. In particular, we learn from algorithms classes that the best sorting algorithms take steps. However, if sorting algorithms are allowed to only exchange consecutive numbers, it is known to be unable to achieve the optimal performance.
Consider a sorting algorithm that only exchanges two neighboring locations (i.e., performing for some ). Prove that there exists a permutation for which must perform at least exchange operations.
Footnotes
-
Note that a one-to-one function is also "onto" if it maps objects from a finite set to itself. ↩
-
Note that here we redefined to start from one. This is usually more convenient when counting whereas starting from is usually more convenient when working with modulo operations as in Number and Algorithms. ↩